How to configure Web Forwarding for Parked Domain Names
How to configure Web Forwarding for Parked Domain Names
When you park your domain names with UK-Cheapest.co.uk, you receive web forwarding facilities that enable you to forward your domain name to another URL.
We offer all three popular Web Forwarding methods
301 Permanent: The recommended search engine friendly redirect to use. This redirect method is Google and SEO friendly. For SEO purposes, “link juice” is passed to the target URL when a 301 redirect is performed. This is not the case with a 302 or Masked redirect.
302 Temporary: Use when you want to temporarily redirect to another URL however you do not want to pass “link juice” to the target. This type of forwarding is rarely necessary, it is not search engine friendly.
Masked/Framed: This method attempts to keep your domain name in the browser address bar whilst displaying the target site in a frame. The advantage of using a frame is that you have control over the meta tag settings. Some target sites do not allow masked forwarding and will show the destination URL in the browser address bar.
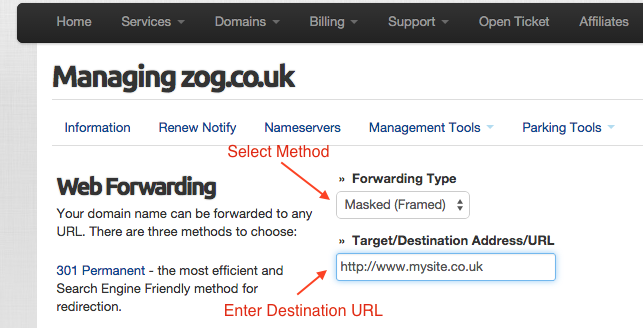
Setting up Web Forwarding is easy
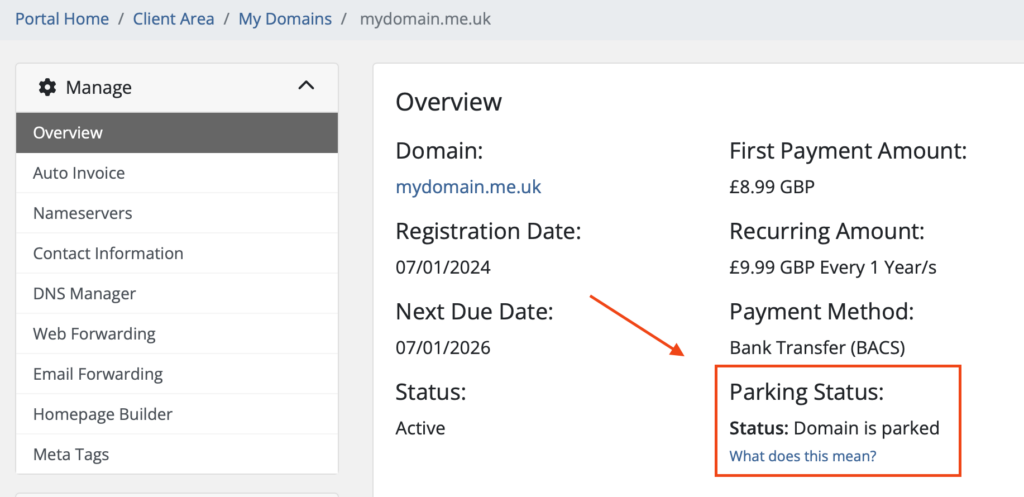
To use the Parking Features, you need to ensure your domain name is parked. If you are not sure it is easy to Check if your Domain Name is parked.
To configure Web Forwarding, simply follow these steps:
- Login to your Client Area and go to Domains > My Domains
- Click Manage on the desired domain name
- Click Parking Tools > Web Forwarding
- Select the desired method from Forwarding Type listbox
- Enter your target URL in the textbox
- Press the Update Web Forwarding button
As long as your domain name is parked, the forwarding feature will work immediately. In some cases you may need to restart your browser if you find you are still forwarded to the previous destination URL.
Advanced Web Forwarding – For FREE
Our Advanced Web Forwarding is provided FREE with all domain names registered or transferred to us. Full control, at no extra cost, where you need it most. There are no limits to the changes you can make.
Domains .co.uk £4.95 .com £7.95